As browser manufacturers gradually continue to monitor third parties, advertising technology companies are increasingly adopting a DNA technique to evade such defenses, which poses a threat to web security and privacy.
Called CNAME Cloaking. The practice of blurring the distinction between first-party and third-party cookies not only leads to the leakage of sensitive private information without the users’ knowledge, but also “increases [the] threat to web security, ”said a group of researchers Yana Dimova, Gunes Acar, Lukasz Olejnik, Wouter Joosen and Tom Van Goethem in a new study.
“This tracking scheme uses a CNAME record on a subdomain so that it is the same site as the site,” the researchers said in the paper. “As such, defenses that block third-party cookies are rendered ineffective.”
The findings are expected to be presented at the 21st Privacy Enhancing Technologies Symposium (PETS 2021) in July.
The emergence of counter-detection measures
For the past four years, all major browsers, with the notable exception of Google Chrome, have included countermeasures to limit third-party tracking.
Apple launched the ball with a Safari feature called Intelligent Tracking Protection (ITP) in June 2017, which sets a new standard of privacy on PC and mobile to reduce the detection of websites by ‘cookies and other websites’ further restrict data. ‘ Two years later, the iPhone maker announced a separate plan called “Privacy Presinging Ad Click Attribution” to make online advertising private.
Mozilla then started blocking third-party cookies in Firefox by default through September 2019 through a feature called Enhanced Tracking Protection (ETP), and in January 2020, Microsoft’s Chromium-based Edge browser followed suit. Then, at the end of March 2020, Apple updated ITP with complete blocking of third-party cookies, including features aimed at reporting fingerprints.
Although Google announced plans early last year to phase out third-party cookies and trackers in Chrome in favor of a new framework called the ‘privacy sandbox’, it is not expected to take effect until 2022.
In the meantime, the search giant is actively working with ad tech companies on a proposed replacement called “Dovekey” that replaces the functionality used by tracking various websites using privacy-centered technologies to place personalized ads on the Internet offer.
CNAME mantle as a scheme for evading tracking
In light of these barriers to killing cookies to promote privacy, marketers have begun to look for alternative ways to evade the absolutist attitude of browser makers against the detection of websites.
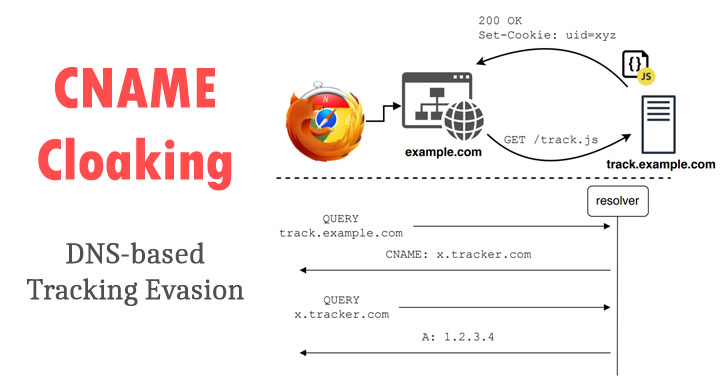
Enter canonical name (CNAME) cloak, where websites use first-party subdomains as aliases for third-party tracking domains via CNAME records in their DNA configuration to bypass trackers.
CNAME records in DNA make it possible to map a domain or subdomain to another (ie an alias), thus making it the ideal way to smuggle tracking code under the guise of a first-party subdomain.
“This means that a site owner can configure one of their subdomains, such as sub.blog.example, to resolve it to thirdParty.example, before resolving to an IP address,” explains WebKit security engineer John Wilander . “This happens under the web layer and is called CNAME cloaking – the thirdParty.example domain is shrouded in sub.blog.example and therefore has the same powers as the true first party.”
In other words, the CNAME mantle makes the tracking code appear to be first party, when in fact it is not, and the resource is resolved by a CNAME that differs from the first party’s domain.
It is not surprising that this detection scheme is rapidly pulling, and has grown by 21% over the past 22 months.
Cookies leak sensitive information to trackers
The researchers found in their study that this technique is used on 9.98% of the top 10,000 sites, in addition to the fact that they have discovered 13 providers of such tracking services on 10,474 sites.
What’s more, the study calls for a “targeted treatment of Apple’s browser Safari” in which advertising technology company Criteo specifically switched to CNAME mantle to bypass privacy protection in the browser.

Since Apple has already built in a lifetime-based defense for CNAME mantle, it is finding will probably reflect more on devices not using iOS 14 and macOS Big Sur, which support the feature.
The most worrying of the revelations is that on 7,377 websites (95%) cookie data leaks were found from the 7,797 websites that used CNAME tracking, all of which sent cookies that contained private information, such as full names, locations, e-mail mailing addresses and even the verification cookies to trackers from other domains without the user explicitly confirming it.
“This is even ridiculous, because why would the user allow a third-party track to receive totally unrelated data, even of a sensitive and private nature?” Olejnik asks.
With many CNAME trackers included via HTTP, as opposed to HTTPS, the researchers also suggest the possibility that a request that sends analytical data to the tracker could be intercepted by a malicious adversary in a man-in-the-box -means (MitM) attack.
Furthermore, the increased attack area created by the inclusion of a tracker as the same site can expose the data of visitors to a website to session fixation and attacks on different sites, they say.
The researchers said they worked with the tracker developers to address the above issues.
Softening CNAME cloth
Although Firefox does not ban CNAME mantling out of the box, users can download an add-on like uBlock Origin to block such rogue first trackers. By the way, the company yesterday started rolling out Firefox 86 with Total Cookie Protection which prevents detection by websites by ‘confin'[ing] all cookies from each website in a separate cookie jar. “
On the other hand, Apple’s iOS 14 and MacOS Big Sur come with additional precautions that build on its ITP feature to protect third-party CNAME garment, though it does not provide a way to unmask and measure the tracking domain to block down. .
“ITP is now detecting third-party CNAME concealment requests and expiring the expiration of cookies set in the HTTP response to seven days,” Wilander recorded in November 2020.
So did Brave Browser, which last week had to issue emergency fixes for an error that occurred due to the addition of CNAME-based ad blocking feature and in the process sent queries for .onion domains to public Internet DNS resolvers. , rather than by Tor nodes. .
Chrome (and by extension other Chromium-based browsers) is the only noticeable omission, as it does not naturally block CNAME and does not make it easy for third-party extensions to resolve DNA queries by retrieving the CNAME records before a request is not sent other than Firefox.
“The Emerging CNAME – Tracking Technique […] evade anti-detection measures, “Olejnik said. It raises serious security and privacy issues. User data is leaking, persistently and consistently, without user awareness or permission. This is likely to lead to the provisions of the GDPR and e-privacy. “
“In a way, this is the new low,” he added.